
According to Russian cybersecurity group Kasperksy, compared to Q1 2021, the number of Distributed Denial of Service (DDoS) attacks in Q1 2022 rose 4.5 times with a considerable number of the attacks likely to be the result of hacktivist activity.
Kaspersky says it operates independently from the Russian government, even as its antivirus software is being investigated in Europe.
The firm continues that the attacks also showed an unprecedented duration for DDoS sessions, particularly those aimed at state resources and banks. Further information has been included in a report issued by Kaspersky.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks are designed to interrupt network resources used by businesses and organisations and prevent them from functioning properly.
They become even more dangerous if the compromised systems are in government or financial sectors, as these services being unavailable has knock-on effects that affect the wider population.
Q1 2022 saw a sudden increase in attacks in late February as a result of the crisis in Ukraine.
Compared to figures from Q4 2021, which had been considered the all-time highest number of DDoS attacks detected by Kaspersky solutions, Q1 2022 saw the total number of DDoS increase by 46%, growing 4.5 times compared to the same quarter in 2021.
The amount of “smart” or advanced and targeted attacks also showed a notable growth of 81% compared to the previous record from Q4 2021. The attacks were not only performed at scale but were also innovative.
Attack Examples
Examples include a site mimicking the popular 2048 puzzle game to gamify DDoS attacks on Russian websites, and a call to build a volunteer IT army in order to facilitate cyberattacks.
“In Q1 2022 we witnessed an all-time high number of DDoS attacks. The upward trend was largely affected by the geopolitical situation,” comments Alexander Gutnikov, a security expert at Kaspersky, referencing the ongoing Russo-Ukrainian war in the region.
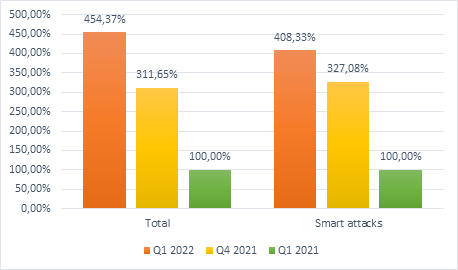
A comparative number of DDoS attacks: Q1 2022 and Q4 2021 as well as Q1 2021. Data for Q1 2021 is taken as 100%
Further investigation conducted by Kaspersky revealed that an average DDoS session lasted 80 times longer than those in Q1 2021. The longest attack was detected on March 29 with an atypically long duration of 177 hours.

A comparative duration of DDoS attacks: Q1 2022 and Q4 2021 as well as Q1 2021. Data for Q1 2021 is taken as 100%
“What is quite unusual is the long duration of the DDoS attacks, which are usually executed for immediate profit. Some of the attacks we observed lasted for days and even weeks, suggesting that they might have been conducted by ideologically motivated cyberactivists. We’ve also seen that many organisations were not prepared to combat such threats. All these factors have caused us to be more aware of how extensive and dangerous DDoS attacks can be. They also remind us that organisations need to be prepared against such attacks,” Gutnokiv concludes.
Read more about DDoS attacks in Q1 2022 on Securelist.
Edited by Luis Monzon
Follow Luis Monzon on Twitter
Follow IT News Africa on Twitter