
Despite the world’s best efforts to get everyone off passwords and onto something else (e.g., MFA, passwordless authentication, biometrics, zero trust, etc.) for decades, passwords have pervasively persisted. Today, nearly everyone has multiple forms of MFA for different applications and websites AND many, many passwords.
The average person has somewhere between three to seven unique passwords that they share among over 170 websites and services.
And, unfortunately, those passwords often get stolen or guessed. This is why I recommend the following password policy guide:

Most computer security experts agree with these policy recommendations, but more than a few readers might be shaking their heads, especially at the recommendations to use 20+ character passwords/passphrases.
Why in the world would anyone need a 20+ character password to protect against password hacking attacks?
In general, password attacks fall into four different major categories:
- Password theft
- Password guessing
- Password hash theft and cracking
- Unauthorized password resetting or bypass
Each will be expanded on below.
Password Theft
Theft of passwords is by far the most prolific type of password attack, usually by social engineering of some type, but it can also be due to malware and hacking tools. The most common theft method is a traditional phishing email where the sender is pretending to be some organization that the potential victim has a relationship with, which contains a message and link prompting the user to type in their real login name and password.
Here is a common example, a password thief’s message pretending to be from Zoom telling me my Zoom service (which I use frequently) has been suspended:
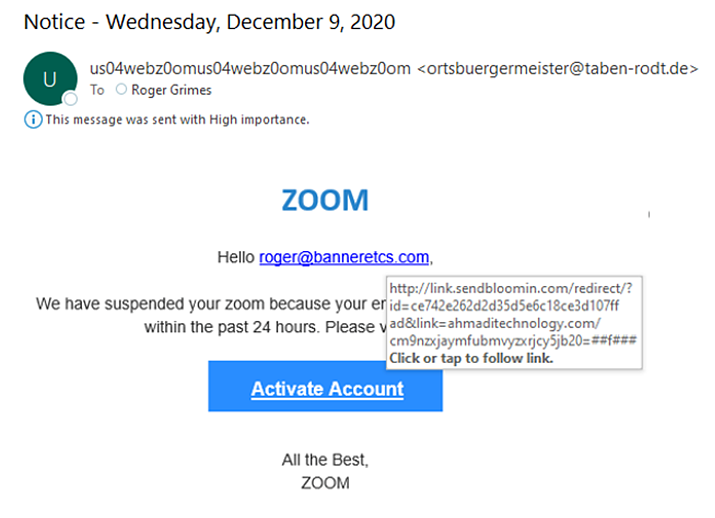
The sender’s email address and the URL link I would have to click are clearly not from Zoom.com, as it would be if the email was legit.
Password Guessing
Passwords can also be guessed. All the attacker needs is an accessible login portal the victim can log into with a login name and password, and the ability to guess multiple times over a long period of time.
Then, the attacker manually guesses or uses an automated password guessing tool. The shorter and simpler the password, the easier it is to guess. If the involved login portal does not have “rate throttling” or “account lockout”, an attacker can guess a dozen to thousands of times a minute.
Since most users’ passwords are less than 12 characters long and not perfectly random, most of those types of passwords can be broken in a period of days to a few months. The average home user rarely changes their password, and most business passwords are only changed once every 90 to 365 days. If an attacker can be given unfettered and unmonitored access to a login portal, they can often keep guessing until they are successful.
One Internet-based company, Akamai, said they saw 61 billion password guessing (e.g., password stuffing) attacks in just 18 months.
Password Hash Theft and Cracking
Another popular password attack is password hash cracking. In most modern-day operating systems, any typed in password is transformed by a cryptographic hash algorithm into a representative hash of the password (i.e., password hash).
Here are some example password hashes of the word ‘frog’ using a handful of hash algorithms supported by popular operating systems:

A user’s password hash is stored in password authentication databases that the operating system uses to authenticate the user. If an attacker can retrieve a user’s password hash, however, they do this, they can guess at (i.e., crack) the password hash by comparing it to a bunch of possible passwords that have already been pre-computed to their hash. This is known as password hash cracking.
Password hash cracking is done externally to the user’s login system. The hacker does not need to be on the victim’s network, and rate throttling and account lockout cannot be implemented to slow down the guessing. Attackers with the appropriate password hash cracking hardware (called password hash cracking rigs), can guess up to many tens of trillions of passwords per second. With that sort of speed, very few passwords below 20 characters will be able to withstand the attack.
It is well-known that within the password hacking community, “normal” human-created passwords up to 18 characters are routinely broken in real-world attack scenarios in days to weeks. However, if the password is truly random, something like what a password manager program could create, then the perfectly random password needs to only be 11-12 characters long to withstand all known password guessing and cracking attacks.
Unauthorized Password Resetting or Bypass
Another common password attack is for a hacker to utilize a method which resets the user’s password or simply bypasses it altogether. Most popular large authentication systems allow users to self-reset their own passwords.
These are needed because one of the most popular support calls is a user forgetting or needing to reset their password. Password calls to tech support are so common that if they were all handled by a human, it would require significantly more resources and money than the involved organization has to spend. So, many/most organizations create or enable a self-help portal that the user can use to reset their password. Unfortunately, hackers know about these two and will use various tricks to reset the user’s password without the user’s permission.
How the hacker is able to do this varies by the authentication system and self-help reset portal, but just know that millions of passwords are reset each year by attackers. The hacker then takes over the account (known as account takeover), changes the user’s password again, and begins using the account in an unauthorized way. Many times, the user is unable to recover the account and it is lost to the hacker forever.
In summary, passwords are compromised by the many tens of millions each year, using password theft, guessing, hash cracking and unauthorized password resetting.
Password Attack Defenses
The password attack defences can be summarized by the following, in order of importance:
- Use phishing-resistant MFA whenever possible
- Mitigate social engineering to prevent password theft
- Use a different, non-guessable password for each site and service
- Use a password manager wherever you are able to allow perfectly random passwords to be created and used, without the user having to create or re-type them
- Where a password manager cannot be allowed, users should create long and/or complex passwords or passphrases, different for each site and service
- All passwords should be changed, at least annually
There are dozens of other good password attack mitigations which should be implemented by users and administrators.
If you can use phishing-resistant multifactor authentication (MFA) instead of a password, try to do that. A hacker cannot steal, guess or bypass your password if you do not have one. It is key to use phishing-resistant MFA whenever possible. Most MFA is easily bypassed by simple phishing attacks, which negates most of the reasons for moving from passwords to MFA.
There is no other single defence that does more to prevent password theft than to mitigate social engineering and phishing.
The second-best thing a user can do is to make sure they use different passwords for every site and service. This prevents one compromised password from more easily allowing additional compromises to other sites and services used by the user.
A perfectly random 11-12-character password, like those created and used by password manager programs, is considered unguessable and uncrackable by any known password guessing attack (i.e., strong passwords can still be stolen). Humans have a hard time creating and using perfectly random passwords, especially when a different one is needed for every site and service. For that reason, every user should use a password manager program when possible. In a perfect scenario, the only password the user would have to create, remember and use, would be the passwords/passphrases needed to log into their device(s) and their password manager program.
The password manager program would handle all password logins after that.
By Roger Grimes, Data-Driven Defense Evangelist at KnowBe4.